As technology advances and security standards improve, clients in the automation industry are transitioning to newer communications standards for both future-proofing and improved plant security. This blog covers the implementation of the MQTT standard, which is known for being simple, secure, and lightweight, with the AWS IoT Core service and the Siemens LMQTT library. The primary goal of this blog is to provide a centralized resource to demystify the setup process.
Note: This blog uses a Siemens S71214 G2 PLC and TIA Portal V20 Update 3, with version 2.3.0 the Siemens “Libraries for Communication”.
Why Certificates?
Instead of user credentials, which can be easily compromised, the industry is slowly shifting towards more secure certificate-based security. Certificates are authorized and signed by a “Certificate Authority” (CA) and come with a public and private key.
A public key is shared openly to encrypt data or verify signatures, while the private key is stored locally by the certificate owner to decrypt data and create signatures, enabling secure communications.
Typically, an MQTT connection is secured through TLS and leverages a unique certificate per device. Devices can share the same certificate, but if one of the certificates is compromised, all devices will need to have their certificates updated.
What’s the Catch?
One way that certificates are more secure is that they have limited lifespans. Each certificate has a specified time frame (usually a decade or more, up to a limit) where it is valid. Upon expiration, communications relying on the certificate will fail until a new certificate is signed by the CA and manually rotated on the device. For Siemens PLCs, this is a manual process that requires a hardware download and downtime.
A similar lifespan issue arises for the CA. The current Amazon Root CA 1 at the time of writing expires January 2038 and has a lifespan of 10-20 years.
However, AWS helps with mitigating this issue by allowing users to remotely monitor and even revoke certificates.
Configuring AWS IoT Core
In AWS IoT Core, every device is registered as a Thing and has associated certificates to secure the communications and “Policies” to determine the permissions a certificate is allowed to have. Before the PLC can communicate with AWS, it must first be configured in the IoT Core with at least one of each (Thing, Certificate, Policy).
Note: It is possible to use user credentials with AWS, but this is less secure and requires the configuration of a custom authorizer and downloading the Amazon Root Certificate to the PLC. More information can be found here: Use API Gateway Lambda authorizers – Amazon API Gateway.
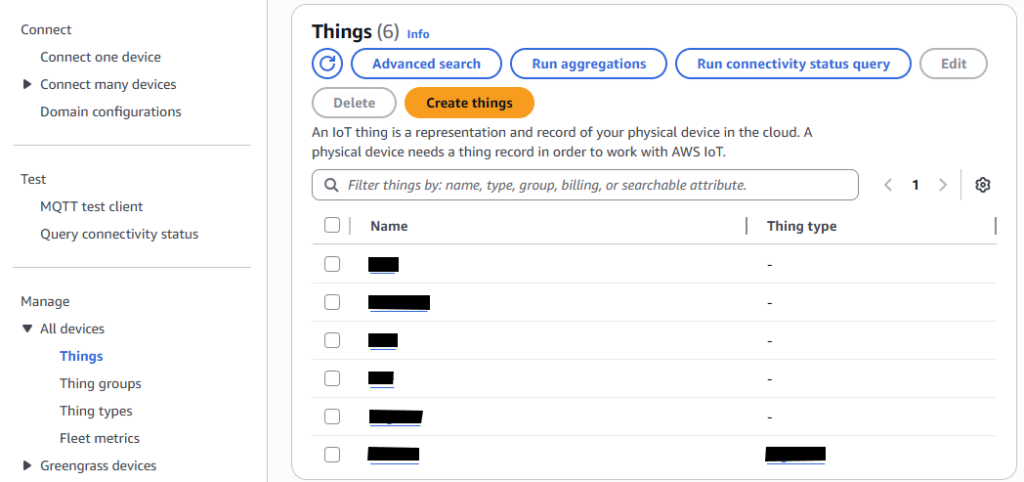
Creating a Thing
A Thing can be created under the “Manage > All devices > Things” menu. Creating a Thing will prompt the user to assign a certificate and a policy. In this example, an auto-generated AWS certificate was used.
Creating a Policy
As part of the steps to create a Thing, you can also create a Policy. Policies are used to Allow/Deny actions that a device can perform when connected using the attached certificate. A policy can be reused across multiple certificates, and a certificate can have multiple attached policies, allowing for flexible configuration.
For testing basic communications and setup, it is recommended that an unrestricted policy be used to allow all policy actions and resources to be accessed (notated by the wildcard character, *). Policies can be updated at any time to remotely modify the permissions of any device.
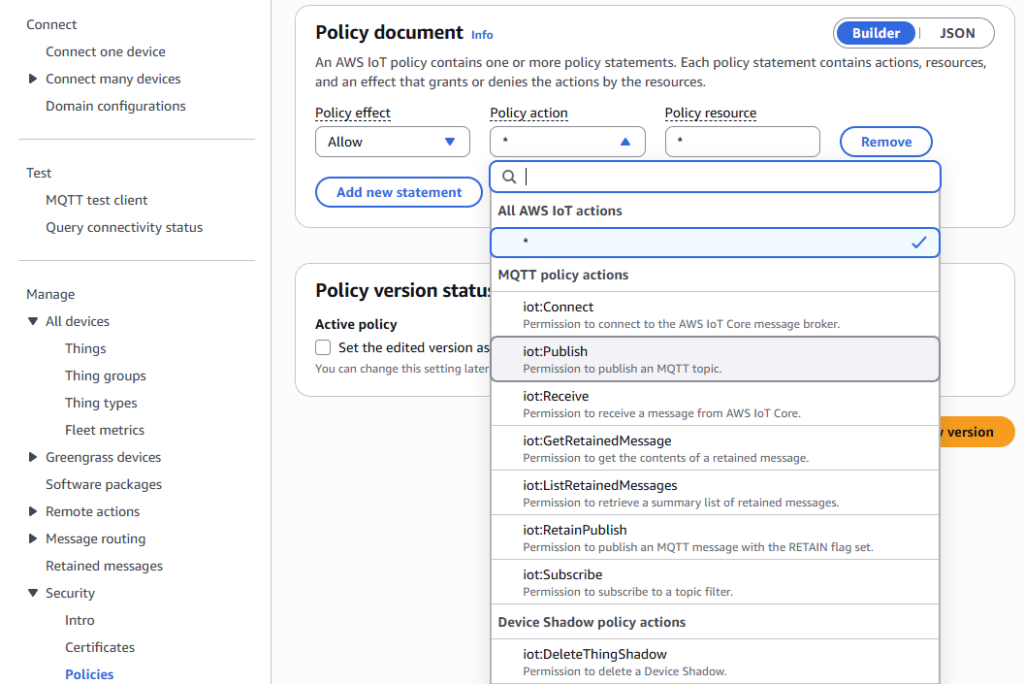
Note: For more information regarding policy configuration, see AWS IoT Core policy examples – AWS IoT Core.
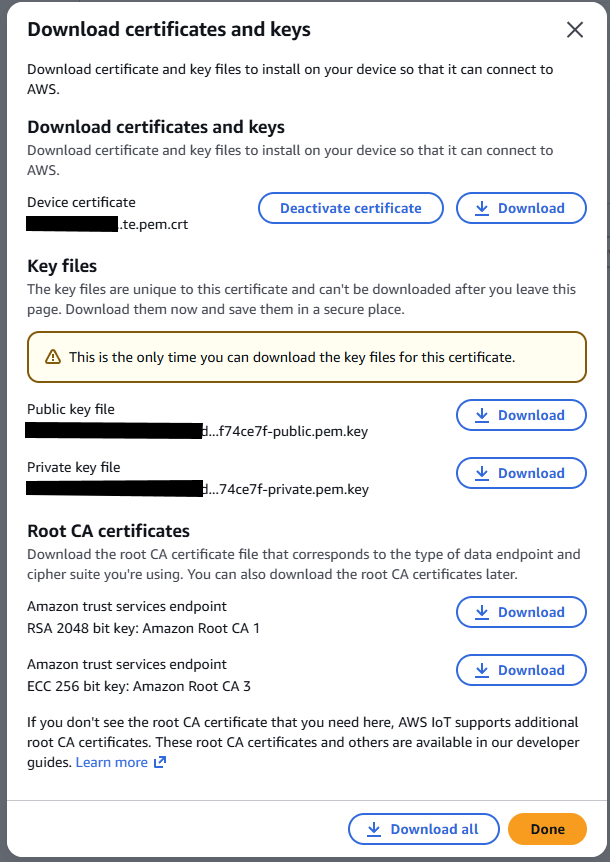
Creating your Certificates
Once a Thing has been created, a pop-up will appear with download links to the generated certificates. Click the “Download All” button to download a copy of the certificate, keys, and root CA certificates. Don’t close the dialog box without downloading a copy of the certificate and keys, as this is the only time they are available for security reasons!
Configuring the Siemens PLC
Configuring the PLC to communicate via MQTT requires 3 steps. First, the LMQTT library must be added to the project and configured for the connection. Next, project security must be enabled to allow the user to access the “Certificate Manager” and import the certificates to the project.
Note: More information and a detailed guide of each step can be found here: Use the SIMATIC controller as an MQTT client – ID: 109748872 – Industry Support Siemens.
Adding the Library to the Project
The LMQTT Library and documentation can be found as part of the communications library here: SIMATIC S7-1500/S7-1200 Libraries for Communication (LCommSuite) – ID: 109780503 – Industry Support Siemens
After downloading the Siemens Libraries for Communication, unzip the file and move the resulting folder to a permanent location. Then, import the “Libraries_Comm_Controller.al20” as a global library into your project.
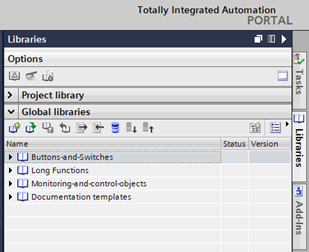
The communications library will then appear. For this blog, only the LMQTT library objects are used. Drag and drop the “LMQTT_Client” object from the Global Library into the “Program blocks” folder of your PLC. All dependencies will automatically be imported into the project along with the library block.
Creating a Data Block
Next, create a Global Data Block to hold the tag values of the LMQTT Client. This can be done by expanding the “Program blocks” folder in the Project tree and clicking “Add new block”. From the dialog box, select “Data Block”, name the block, and choose “Global DB”.
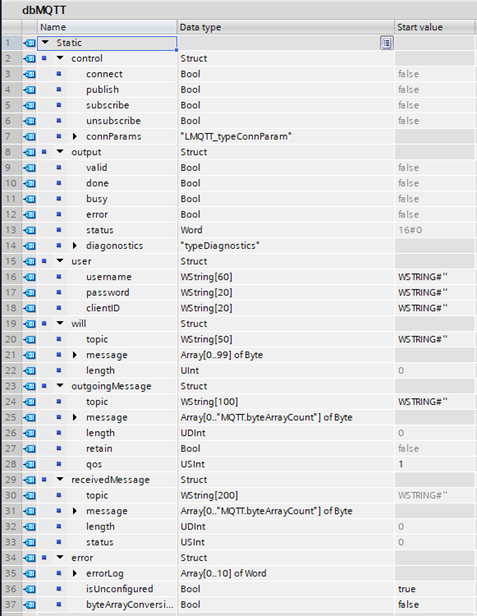
The Data Block used by our example project is shown below. Some notes on our implementation:
- Outgoing and Received message have a constant defining the length of the message byte-array.
- The error struct is used to log a history of errors and record the status of the system and are not mandatory.
Configuring Connection Parameters
The connection parameters in our example are configured as follows:
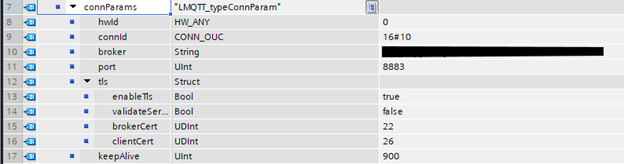
Some notes on our configuration:
- “hwId” is best left as 0, as this will allow the library to select a suitable hardware interface automatically. To specify it directly, Hardware IDs can be found by going to the “Device Configuration > Properties > System constants” tab of your PLC.
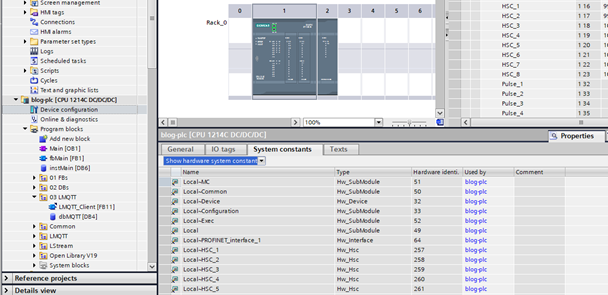
- “connId” must be unique for each connected device.
- “broker” will be your unique AWS IoT Data Endpoint. This can be found in the AWS Portal under the “Settings” menu.
- “port” for our application will be 8883 (certificate authenticated pub/sub). A list of standard AWS ports are found here: Device communication protocols – AWS IoT Core.
- The “tls” settings enable encryption. The important settings here are that the broker certificate and client certificate numbers match the certificates in the Certificate Manager (covered later in the blog).
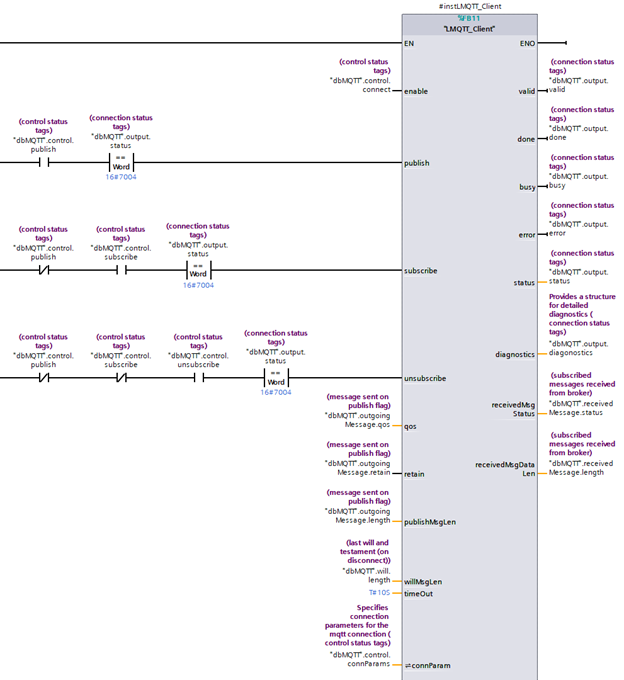
Connecting the LMQTT Client Function Block
An instance of the LMQTT Client function block can be created by dragging an instance of “LMQTT_Client” into any LAD block on the PLC and linking the corresponding tags in the database. An example of how the tags can be linked is shown below:
Enabling Project Security & Importing Certificates
To enable project security, navigate to the PLC’s “Properties > General > Certificate manager” menu and enable the “Use global security settings for certificate manager” setting.
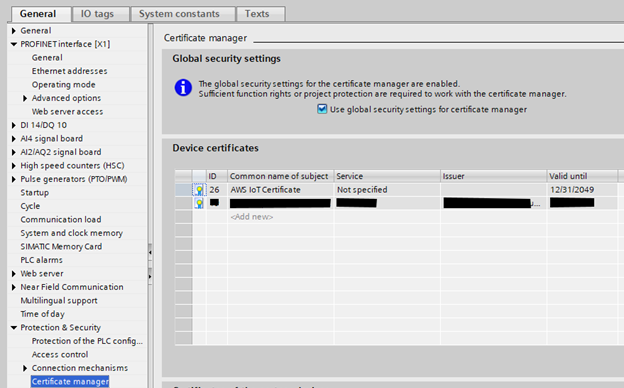
Next, enable project security by navigating in the Project Tree to “Security settings > Settings > Project protection” and password-protect the program. This is necessary to enable the project “Certificate manager” menu under “Security Settings > Security features.”
Before the certificate is imported into TIA Portal, the AWS client certificate and private key must be merged using a text editor. This can be done by opening both the *.pem certificate and the private.key file and pasting the private key in the line below the certificate. After doing so, your certificate file should look like the one below:

To import a certificate, navigate to the “Trusted Certificates and root certificates” menu in the project “Certificate Manager”, right-click the table and select import. The two files that will be needed are the:
- Amazon Root CA1 (SHA-256)
- AWS IoT Certificate (Modified with key appended to certificate)
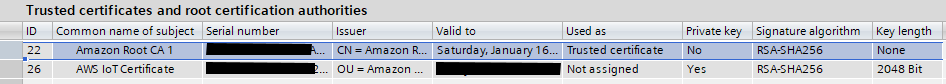
Once complete, the two certificates should appear as follows:
- The ID of the “Amazon Root CA 1” MUST correspond to the “brokerCert” in the connection parameters.
- The ID of the “AWS IoT Certificate” MUST correspond to the “clientCert” in the connection parameters.
Next, return to the PLC “Properties > Certificate manager” and add the IoT Certificate under “Device certificates” and the Root CA1 certificate as a “Certificates of partner device.”
Finally, the IP, gateway, and time settings of the PLC need to be configured before downloading to the PLC.
Operation of LMQTT Client
The LMQTT Client can be directly controlled by monitoring the runtime values of the Data Block. To start a connection, bring the “connect” input on the Client high and wait for the block to connect.
The status of the block can be seen by monitoring the “output > diagnostics > status” tag. A tag value of 16#7004 indicates a successful connection.
The publish/subscribe/unsubscribe signals are level-triggered, and only a single command is allowed to be active at any given moment, or else an error will occur.
A message can be published to a topic by setting the topic, populating the byte array and setting the data length, and setting the “publish” control signal. Any MQTT client subscribed to the same topic and connected to the AWS Endpoint will be able to see your published message.
Troubleshooting Common Errors
Note: An additional guide accompanying the LMQTT library is the Cloud connection – simple and secure with SIMATIC S7-1200/S7-1500 – ID: 109772284 – Industry Siemens Support by Siemens, which provides more detail about configuring an AWS broker and setting up the PLC project from scratch.
The LMQTT Client is timing out when trying to connect
This is most likely caused by an incorrect connection parameter or improper network configuration on the PLC. Some steps to try to remedy this error:
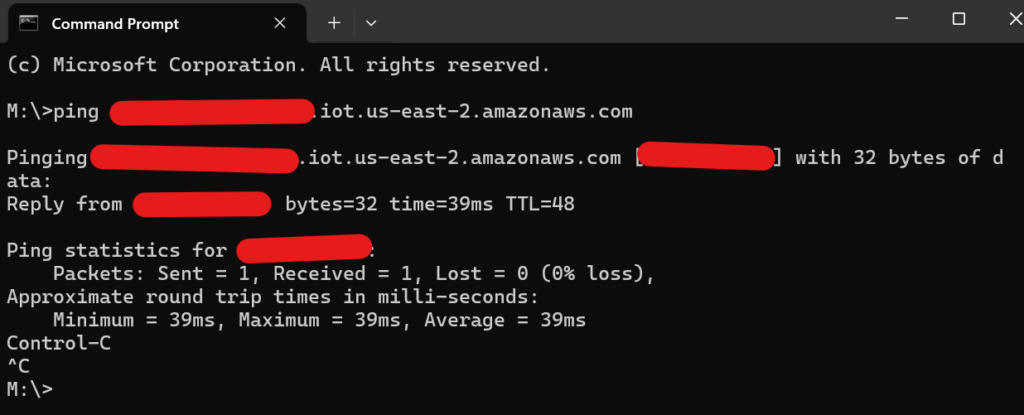
- Check that the AWS IoT Data Endpoint is pingable from the device network.
- A known issue of older versions of the LMQTT library is that the broker string needed to be terminated with a period, but this is resolved in current versions of the library.
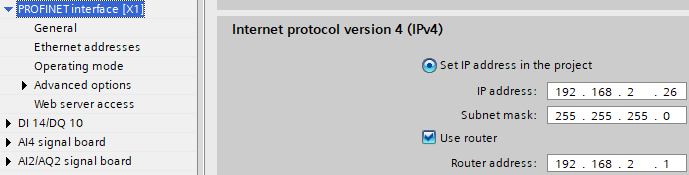
- Check your PLC network configuration. Since the PLC needs an internet connection to reach the AWS Endpoint, the correct router address is mandatory. To find the router address, run a “ipconfig” command in Command Prompt and look for the “Gateway” setting for your network adapter while connected to the PLC network.
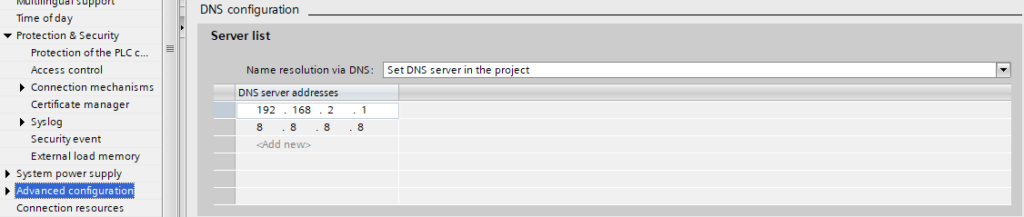
The DNS server might not be properly configured. This will prevent the PLC from resolving the Endpoint. DNS servers can be configured in the PLC “Properties > Advanced Configuration” menu. The DNS addresses can be your router gateway or a trusted server such as Google (8.8.8.8).
The LMQTT Client is stuck in a reconnection loop
A connection loop is a sign that the certificate authentication or AWS policy is configured incorrectly. Ensure that the certificate is set up properly and that the Client block is not attempting to connect with a denied Publish topic for the Will topic for the active AWS Policy.
I want to test my MQTT connection without the PLC
There are many free downloadable MQTT clients that can be set up on your computer, such as MQTTx or MQTT Explorer.
Conclusion
Although the setup process is more complex than traditional methods, secure MQTT communications from a PLC to the cloud can allow remote communications that would cause security risks with traditional methods. At its core, MQTT is a secure and lightweight protocol that is versatile and can suit the needs of hobbyists and industry alike.
Ready to take your Automation project to the next level? Contact us today to learn more about our solutions and how we can help you achieve your goals.







